| Product Type | Network Security Integration Software |
| Form Factor | Software (Downloadable/Virtual) |
| Supported Platforms | Cisco Firepower, Splunk Enterprise |
| Use Case | Security event ingestion and analysis in Splunk from Cisco Firepower |
| Recommended Users | Security Analysts, SOCs, Enterprises, Government Agencies |
| Power Requirements | |
| License Type | Perpetual or Subscription (based on purchase) |
| License Qty | 1 license per Splunk integration |
Cisco eStreamer eNcore for Splunk
Key Benefits
AI-Powered Summaries from Online Customer Reviews
Eye-Insights™ are generated by proprietary AI that analyzes real online customer reviews to highlight top pros and key product features. While we aim for accuracy, insights are provided “as-is” and individual results may vary.
- Enables seamless integration of Cisco security telemetry into Splunk for streamlined analytics
- Complies with TAA standards, making it suitable for public sector and regulated industries
- Built by Cisco, ensuring optimized compatibility with Firepower Network Security appliances
Product Overview
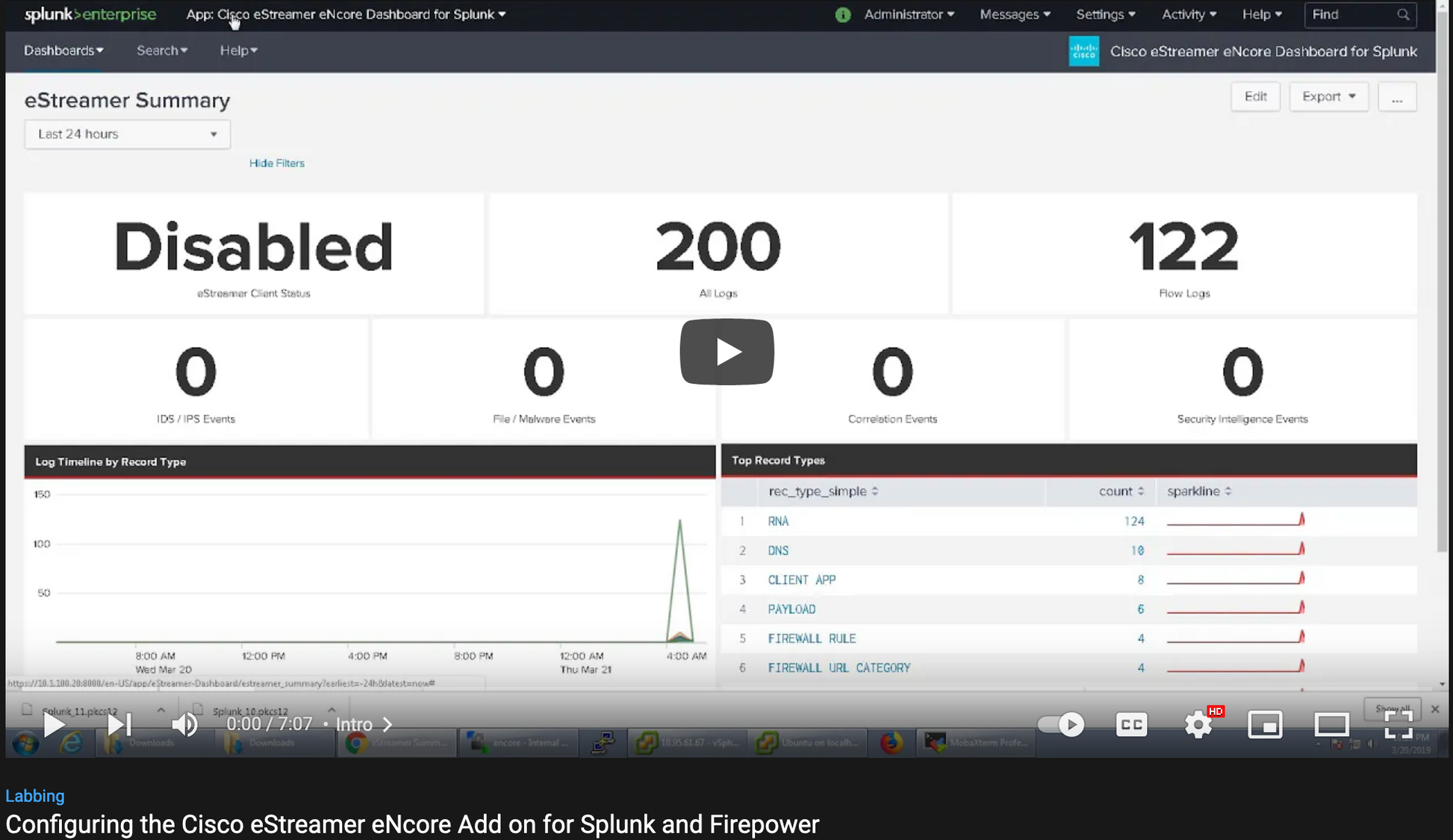
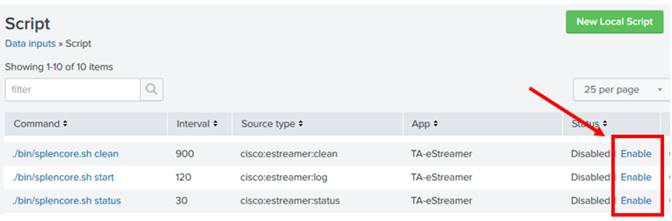
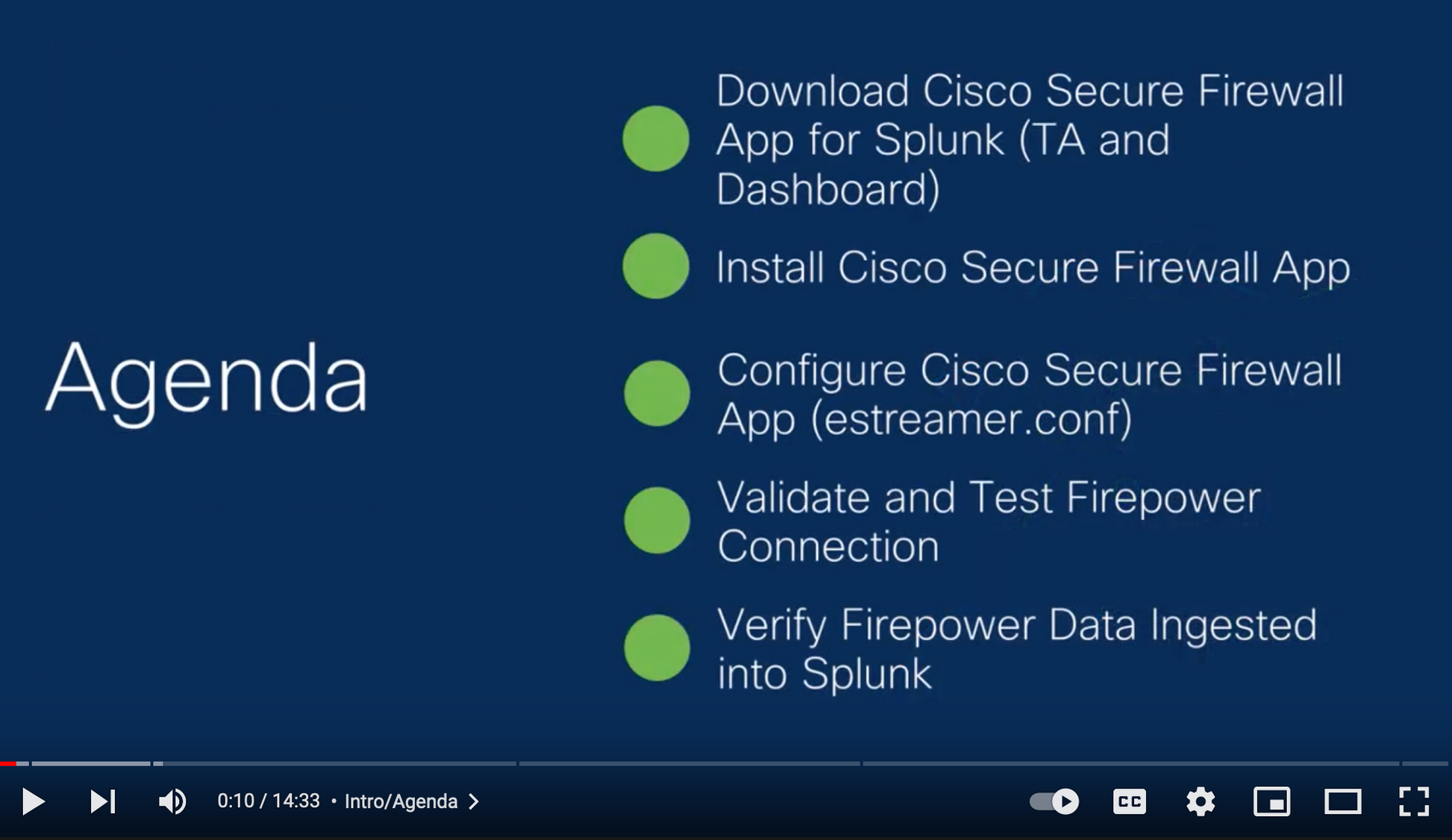
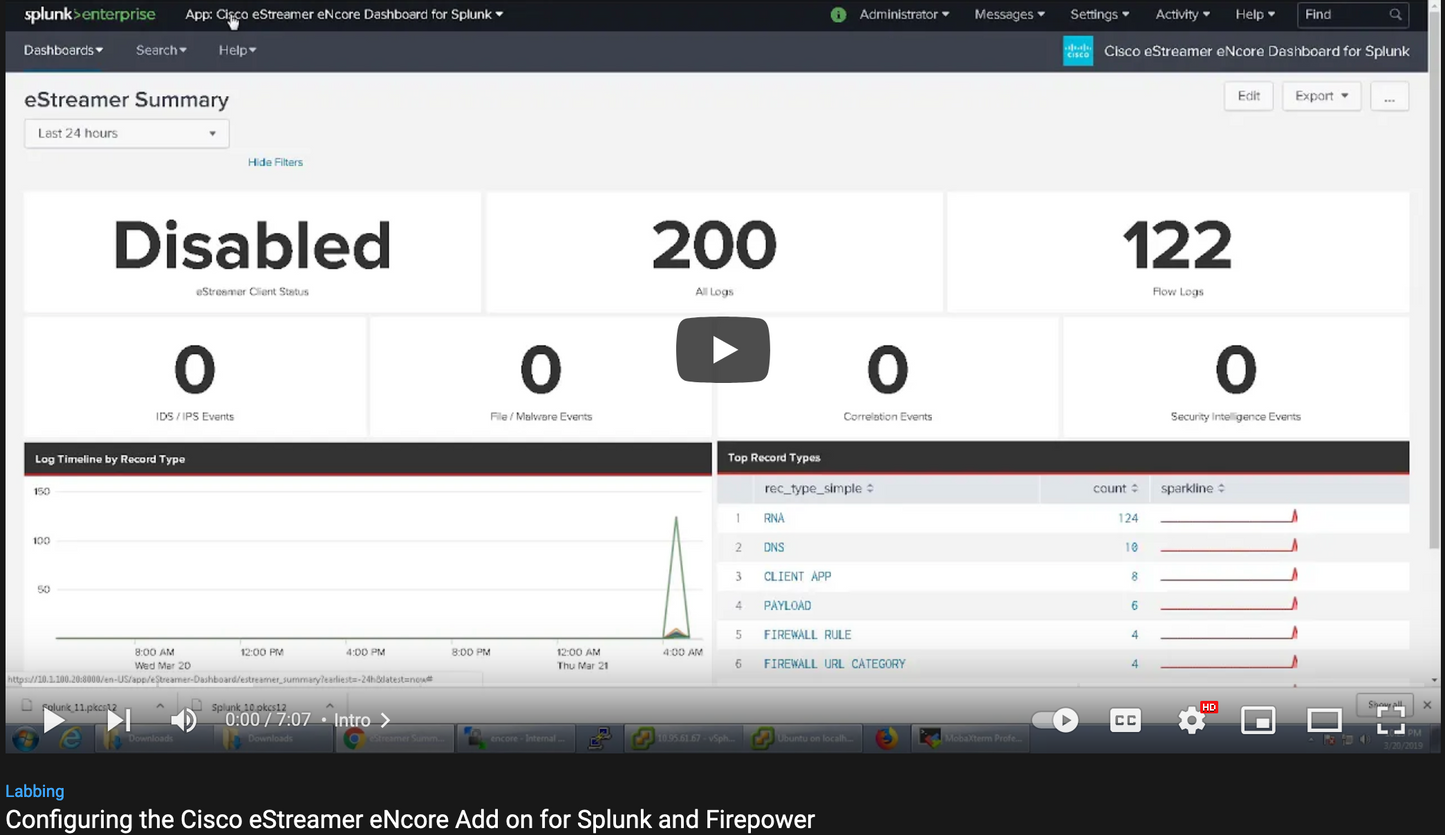
Cisco eStreamer eNcore for Splunk is a specialized network software tool developed for users of Cisco Firepower appliances and Splunk. Designed to efficiently ingest and translate eStreamer data, it enables advanced security event analysis and visualization within the Splunk ecosystem. By leveraging native integration capabilities, this solution streamlines the data pipeline from Firepower sensors to actionable security dashboards.
This software supports users in forensic analysis, threat hunting, and compliance auditing by providing granular visibility into network activity and real-time threat telemetry. Since it complies with Trade Agreements Act (TAA) standards and originates from the United States, it is ideally suited for government agencies and regulated environments. Whether used by security operations centers (SOCs) or enterprises with layered defense strategies, it optimizes performance and ensures a seamless workflow across Cisco and Splunk platforms.
While limited details are available, it is evident that the solution is purpose-built to reduce complexity in event correlation and to accelerate incident response using Splunk's powerful data processing capabilities.
Specifications
Product Overview
Wireless Features
| Wi-Fi Standards | |
| Antennas | |
| Wireless Frequency Bands |
Compliance & Origin
| Country of Origin | United States |
| TAA Compliance | Yes |
| Certifications | Compatible with TAA deployment environments |
| Software Origin | Cisco Systems, Inc. |
| GovCloud Eligible | Yes |
Advanced Security Features
| Data Encryption | Encrypted telemetry via eStreamer protocol (SSL-based) |
| Security Event Parsing | Yes, supports detailed parsing for visualization and SOC workflows |
| Firewall Event Ingestion | Yes (from Cisco Firepower and ASA w/ FirePOWER) |
| Threat Intelligence Compatibility | Integrates with threat feeds via Splunk |
| Malware Detection Events | Yes (supported if enabled in Firepower policy) |
| IDS/IPS Event Support | Yes (Intrusion Event ingestion supported) |
| Compliance Monitoring Support | Yes (Meets forensic and auditing requirements) |
Interfaces
| Data Integration Interface | eStreamer (Cisco Encrypted Streaming Telemetry) |
| Supported Event Transport | SSL-encrypted TCP |
| Supported Data Source | Cisco Firepower Threat Defense (FTD), Cisco ASA with FirePOWER Services |
| Supported Log Types | Intrusion events, Connection events, File and Malware events |
| Data Transfer Function | Push and Pull (based on configuration) |
Physical & Environmental
| Product Dimensions | |
| Software Footprint | Lightweight Python-based package |
| Operating System Required | Linux or Splunk-supported OS (e.g., Red Hat, CentOS, Ubuntu) |
| Operating Temperature | |
| Relative Humidity | |
| Virtual Appliance | No (Installed as an add-on or stand-alone script) |
Cloud Management & Licensing
| Management Interface | Command Line (Python), Splunk Web Interface |
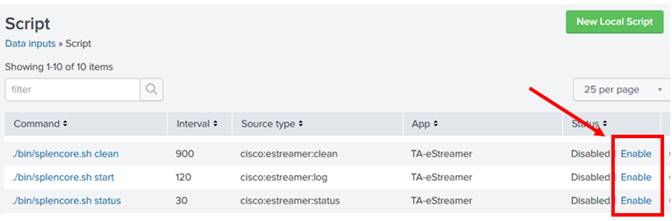
| Splunk Integration Method | Modular Input & Python Data Ingestion Script |
| Cloud Ready | Yes (compatible with Splunk Cloud) |
| Included Software Components | eNcore (Python application and Splunk TA) |
| Licensing Model | Per-connection or per-appliance monitoring scope |
| Compatibility | Splunk Enterprise 6.x and later |
| Automatic Updates | Manual installation of updated modules |